Cyber Security Incident Response Services Built for Speed, Recovery and Reputation
When a cyber incident strikes, every second counts. DSP’s cyber security incident response services give you immediate access to expert support, containment, and recovery. From ransomware to advanced persistent threats, we’re here to restore control, reduce damage, and get you back to business fast.
Resilient, reliable, responsive
DSP's cyber security incident response solutions are designed for organisations that need more than just reaction; they need a trusted partner in recovery. We combine technical depth with strategic insight to help you prepare, respond, and recover from cyber threats that target your infrastructure, databases, applications, and cloud environments.
Whether you’re managing mission-critical workloads, hybrid cloud environments, or on-premise systems, our approach integrates deep technical expertise, real-time coordination, and regulatory understanding to deliver peace of mind when it matters most.
-
24/7/365 Emergency Response: Rapid engagement through a dedicated hotline or secure channel
-
Pre-Breach Preparation: Incident response planning, runbooks, and tabletop exercises tailored to your environment
-
Real-Time Incident Management: Immediate triage, containment, eradication, and communication support
-
Post-Incident Recovery: Root cause analysis, system hardening, and improved resilience strategies
Get in touch with one of our experts
Discover our cyber security incident response services
Incident response and recovery
Responding to cybersecurity incidents demands more than forensics; it requires a partner who understands regulatory complexity, organisational structure, and the evolving tactics of threat actors. With increasing interconnectivity, strict regulations like DORA and NIS2, and growing public scrutiny, operational resilience is now a critical priority, especially for highly regulated industries and OT environments.
Our retainers offer 24/7 global access to specialist teams and a modular, customisable structure. We focus on year-round engagement, using workshops, real-time virtual collaboration, and threat intelligence to ensure familiarity and rapid response when it matters most. Unused hours can be repurposed for preparedness, giving you maximum commercial value and peace of mind.
Cyber security threat hunting and detection engineering
Understanding your cybersecurity posture is essential. As attacks grow more sophisticated and harder to detect, organisations must take a proactive approach to identify vulnerabilities and hidden threats within their IT environment.
Many leaders worry their systems have become too complex to secure, allowing attackers to remain undetected for extended periods. Our discovery and detection services provide deep visibility into cyber risks and indicators of compromise by analysing data from endpoints and external sources, enhanced with proprietary threat intelligence. We help you uncover missed threats, assess risk exposure, and deliver clear, actionable remediation guidance to strengthen your defences.
Ransomware readiness and recovery
Ransomware remains the most significant cybersecurity threat for organisations, with increasingly sophisticated, human-operated attacks causing major operational disruption and financial loss. These attacks often involve data theft and system encryption, pressuring victims to pay large ransoms. However, many businesses remain unprepared, not just in defence, but in recovery.
Cybersecurity and business resilience functions often operate in silos, leading to gaps that ransomware can exploit. Traditional resilience plans typically overlook cyber threats, and tools like data replication can unintentionally spread malware. To effectively protect against ransomware, organisations must implement strong preventative controls, gain visibility into their IT estate, and build resilience strategies that enable rapid containment and recovery. This requires cross-functional collaboration, realistic scenario testing, and clear recovery plans that consider both technical and operational impact. End-to-end preparation is key, because in a ransomware attack, response is just the beginning.
Crisis management
Being “crisis-ready” is essential in a world where cyber attacks are increasingly frequent, complex, and damaging. While preventing every attack is impossible, true cyber resilience means being able to absorb disruption and respond quickly to minimise impact. This requires more than technical controls; it demands a well-prepared, well-rehearsed organisation.
Our approach helps you assess gaps, identify critical business services, and build cyber response plans and playbooks. We deliver tailored crisis exercises and leadership training to strengthen decision-making under pressure. During an incident, we provide expert guidance and hands-on support at all levels, from technical teams to the board. Afterwards, we conduct a full post-incident review, analysing root causes, impact, and effectiveness of your response to help you recover stronger and with more resilience.
Our Customer Satisfaction Score proves we’re a safe pair of hands.
Why DSP’s cyber security incident response delivers more
We know that during a cyber crisis, it’s not just about stopping the threat, it’s about how fast and confidently you can recover. That’s why our Cybersecurity Incident Response services go beyond technical containment to support board-level decision-making, stakeholder communication, and post-event improvement.
-
Certified partner for all environments: We understand your enterprise stack, from engineered systems to cloud-native.
-
Rapid SLA guarantee: When you activate our retainer, our response team is mobilised immediatley.
-
Use retainer hours proactively: Unused hours can be redirected to simulation testing, detection enhancements, or training.
-
Threat intelligence-driven: We keep you ahead of emerging cyber risks with contextual intelligence and proactive alerts.
-
Built-in continuity planning: Cyber recovery runbooks integrated with business continuity and disaster recovery (BCDR) planning.
-
Global reach, local expertise: Support based locally to you with international reach across Europe and North America.
Trusted by some of the biggest brands


.png)
.png)

.png)

.png)

.png)


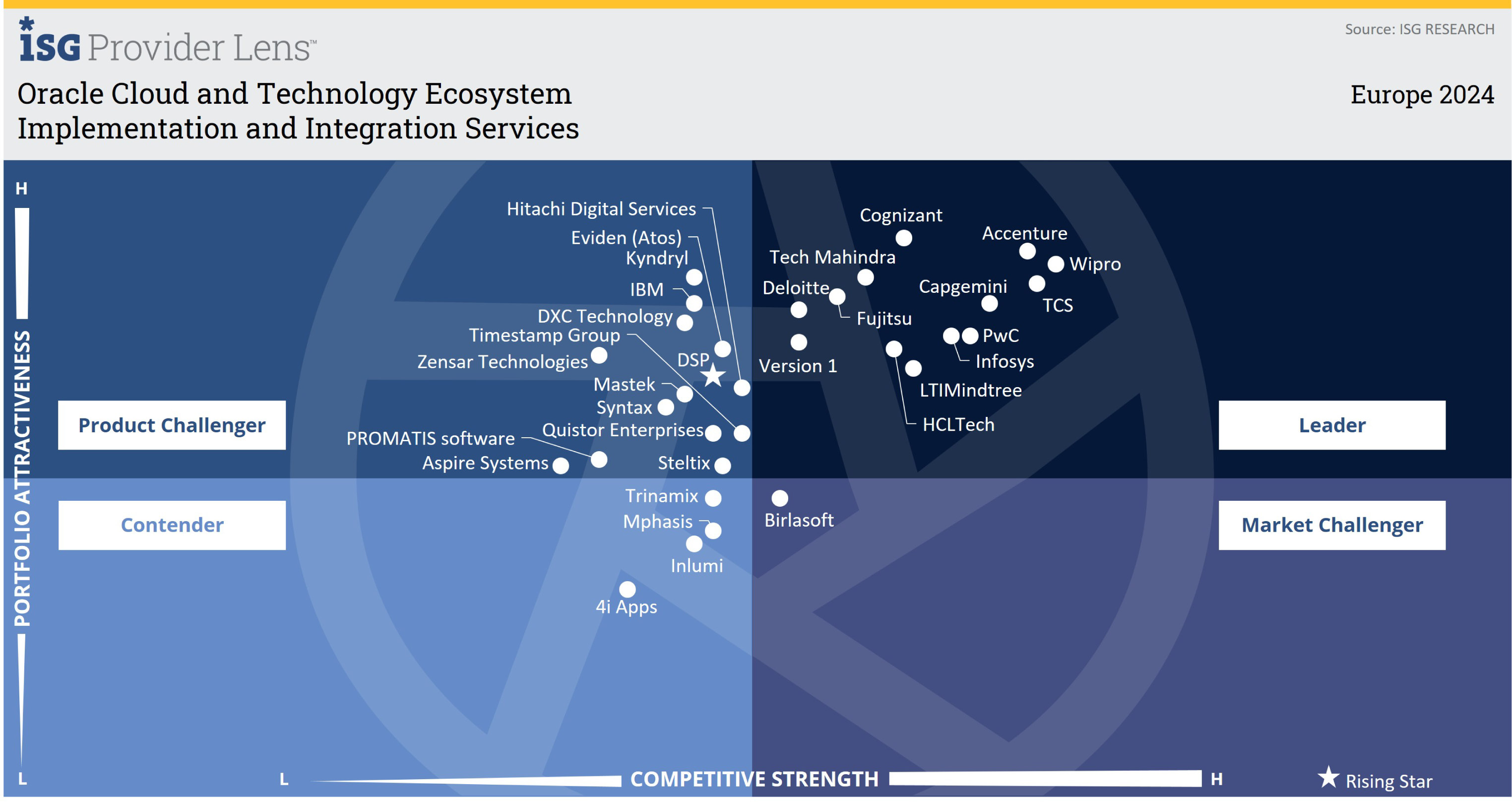
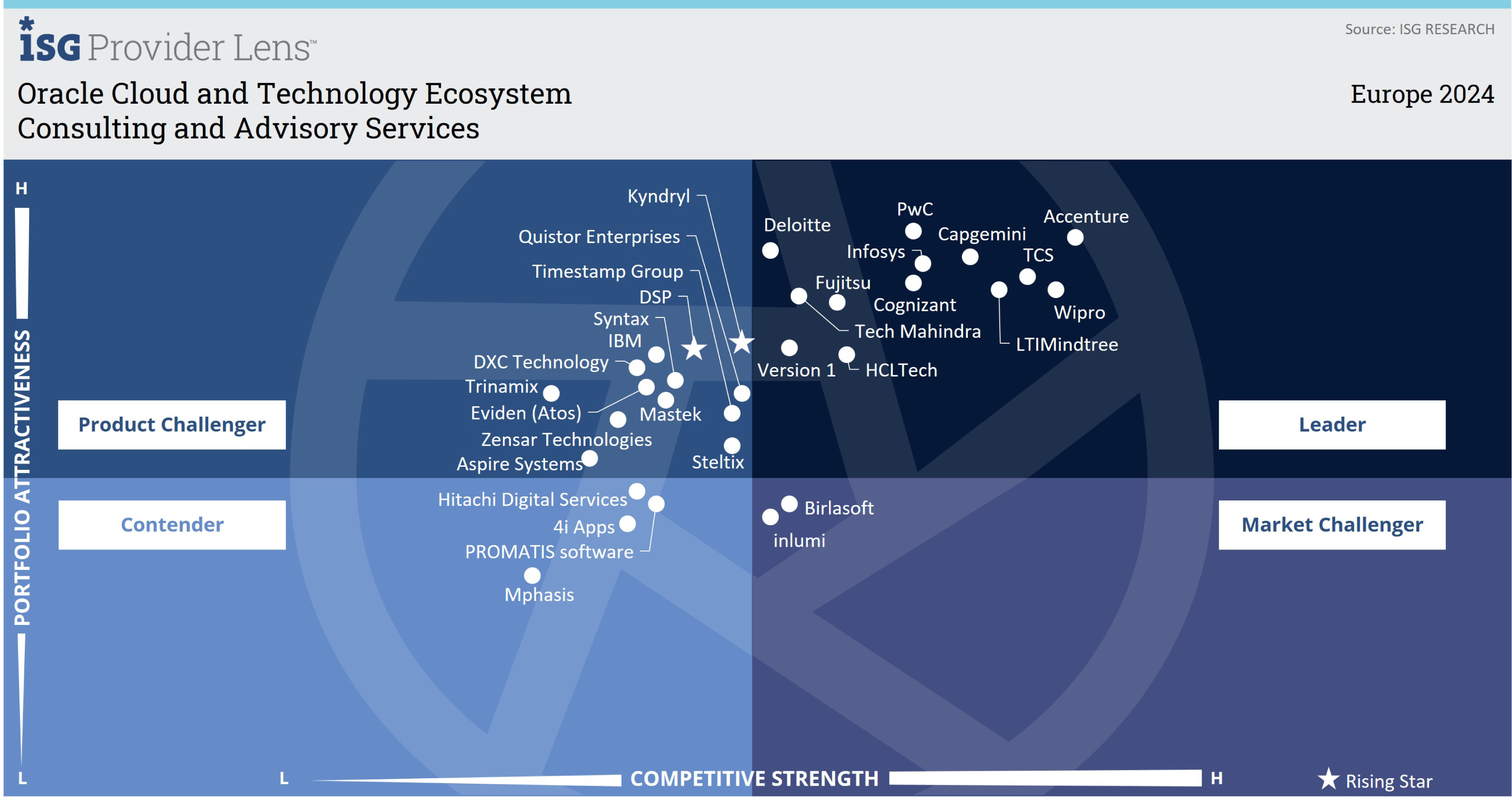
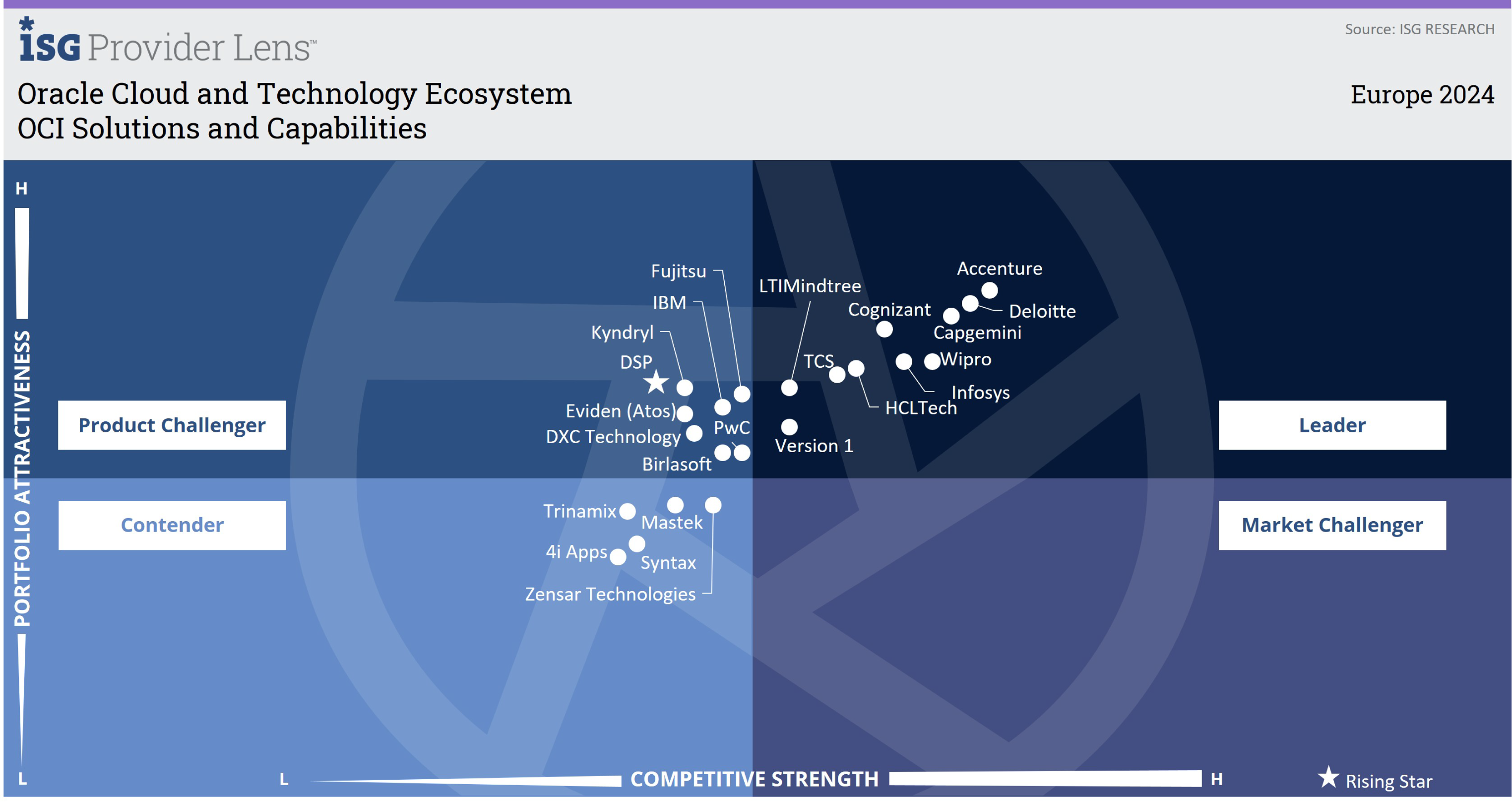
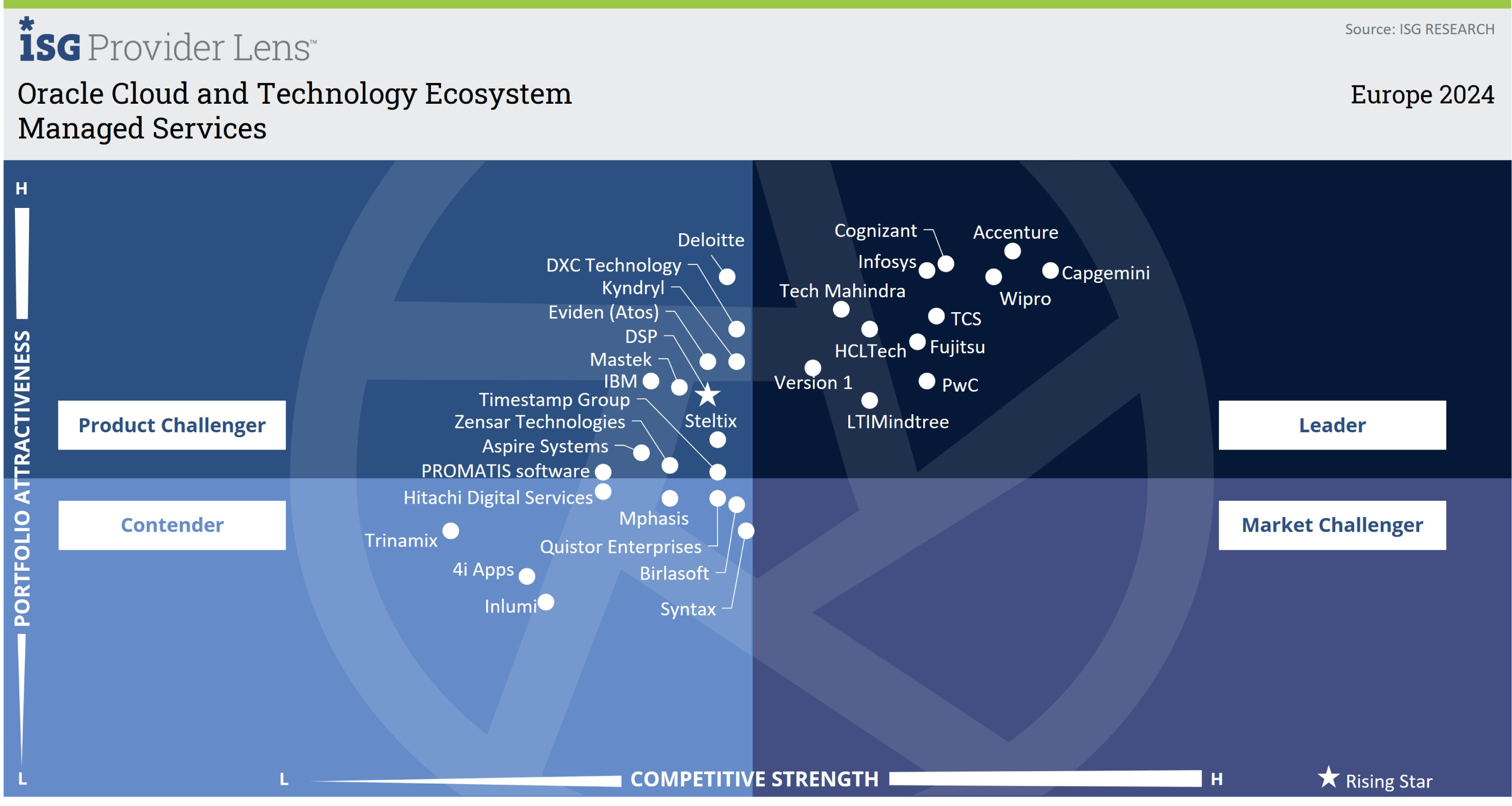
DSP is the only company to be identified as a ‘Rising Star’ in all four quadrants in the latest ISG's Provider Lens™ evaluation for Oracle Cloud and Technology Ecosystem Europe 2024.
"DSP pairs disciplined engineering with AI-centric innovation, integrating OCI workloads across clouds while safeguarding them with ML-powered vulnerability scanning."
Roman Pelzel
Lead Analyst ISG
Strengthen your data security posture
Whether at rest or in transit, your data must be secure, compliant, and auditable. DSP’s Database Security Assessments provide clarity and confidence by identifying vulnerabilities, reducing risk, and helping you benchmark your estate against best practices and compliance standards. It can also uncover opportunities to optimise performance and reduce long-term operational costs.
Standard Database Security Assessment
A foundational check to ensure your database is secure and compliant.
- Patch level and utilised features
- Encryption (wallets, FIPS modes)
- Network encryption configuration
- OS settings (e.g. CMAN remote admin, diagnostic destinations)
- User accounts, roles, and privileges
- Core database configuration
Database Security Assessment Plus
A deeper dive for organisations needing comprehensive security validation. It includes everything in the Standard Assessment, plus:
- Authorisation control
- Fine-grained access control
- Database auditing
- Advanced analysis of user accounts and access patterns
Our thinking
 JavaScript
JavaScript
Adding Payments to Oracle APEX Using Stripe
Adding payments to an Oracle APEX application is one of those things that sounds intimidating, but in reality follows a fairly standard pattern once...
Jamie Lambertstock25-Feb-2026 15:58:29
 Oracle Managed Service
Oracle Managed Service
What are the Benefits of outsourcing Managed Services?
In an era where data is often called the "new oil," managing the infrastructure that stores and processes that data has never been more complex. For...
Doria Sacer16-Feb-2026 14:53:32
 Mobile applications
Mobile applications
Mobile-Compatible vs Mobile-Centric APEX Apps
Oracle APEX is an excellent low-code platform that can display content on a variety of device types and screen sizes, including desktop, tablet, and...
Michael Pickering11-Feb-2026 15:41:52
 Microsoft
Microsoft
Modernising Data Integration: The Benefits of Migrating from ADF to Microsoft Fabric
As organisations modernise their data platforms, traditional data integration tools are being re-evaluated in the context of cloud-native analytics...
Pujitha Chennupati29-Jan-2026 09:08:04

Paul Coyle
Technical Director


.png?width=250&height=56&name=stonewater-logo%20(1).png)


