
Keep Your Data Secure Throughout the Cloud Lifecycle
Oracle Cloud
Contents
- Introduction
- A two-pronged security strategy for security posture management
- Oracle Cloud Infrastructure security designed for all users and data
- Automating security in a cloud compartment with Oracle Security Zones
- A holistic picture of security and risk posture management with Oracle Cloud Guard
- Shifting the cloud security shared responsibility model with Oracle Security Zones
- Stepping up security in Oracle Cloud Infrastructure
- Conclusion
Introduction
Businesses can no longer ignore the advantages of the cloud as it provides lower infrastructure spending costs, greater business agility, and flexible scalability. Consequently, more businesses than ever are moving their mission-critical enterprise workloads to the cloud.
It has been reported in the Oracle and KPMG Cloud Threat Report that 76% of businesses use Infrastructure as a Service (IaaS), almost 90% use Software as a Service (SaaS), and 50% anticipate moving all of their data to the cloud in the next two years.
Unfortunately, increased cloud adoption still has costs, despite the advantages it offers. As companies' IT teams and cloud service providers work to secure their data, many have created new security blind spots, which is causing areas of concern.
It is forecasted that by 2025, % of cloud security failures will be the customer’s fault.
Enterprise cloud security and privacy administrators are expected to have a thorough understanding of cloud security services, be able to deploy them without endangering business continuity, and correctly manage secure resource configurations in a constantly changing environment. However, even with a well-trained team of cloud security experts, it can be challenging to overcome this obstacle when you consider the majority of public-cloud tenants mix on-premises, cloud, and, multicloud deployments at scale.
A new approach to security posture management
Oracle wants cloud security and privacy administrators to be confident when securing cloud infrastructure workloads. Therefore, security needs to be simple to deploy and maintain. Security should also be automated and sophisticated enough to protect the most important data and workloads, while also allowing security professionals to apply their expertise easily to meet security objectives.
For this reason, Oracle Cloud Infrastructure is releasing new security cloud services for cloud security posture management (CSPM) and cloud security orchestration and automation and remediation (SOAR) of Oracle Cloud Infrastructure tenancies.
Cloud security posture management removes the common barriers to securing cloud services. It is made possible through the incorporation of security expertise, the centralisation of configuration management and monitoring, and the automation of remediation workflows.
Oracle Security Zones
Special compartments created to enforce both implicit and explicit security policies.
Oracle Cloud Guard
A scalable data processing security service that serves as the command centre for Oracle cloud security posture management. Oracle Cloud Guard provides a complete picture of a customer's tenants' security and risk posture in Oracle Cloud Infrastructure.
Customers now have the option to steer clear of cloud services that are improperly configured at various stages of the resource configuration lifecycle thanks to Oracle Security Zones and Oracle Cloud Guard, which represent a new approach to cloud security.
Oracle Security Zones focuses on a preventative strategy that can prevent the creation of resources that violate security requirements, whereas Oracle Cloud Guard provides a detect-and-respond framework that allows for more context before remediation is implemented.
Oracle Security Zones and Oracle Cloud Guard are cloud security services that support the entire Oracle Cloud Infrastructure ecosystem, including traditional console and programmatic user interfaces (such as OCI, API, CLI, SDK, etc).
This two-pronged strategy enables continuous security and risk monitoring across the entire Oracle Cloud Infrastructure ecosystem while assisting Oracle Cloud users in deploying securely right away.
Oracle Cloud Infrastructure security designed for all users and data
Oracle Security Zones and Oracle Cloud Guard enhance Oracle Cloud's security automation and embedded expertise, making it simple for any cloud user to operate securely.
Oracle Cloud Infrastructure is an infrastructure-as-a-service (IaaS) offering built with security in mind.
The security includes isolated network virtualisation, which provides superior customer isolation over previous public-cloud designs. As well as hardware root-of-trust technology, which reduces risks from compromised firmware. From the physical hardware in our data centres to the web layer, Oracle Cloud Infrastructure benefits from tiered defences and heavily secured operations.
Many of these safeguards also work in conjunction with third-party clouds and on-premises solutions to help secure modern enterprise workloads and data wherever they may reside.
Oracle Security Zones and Oracle Cloud Guard, like the Oracle public-cloud design, continue to emphasise security themes such as resource configuration and activity monitoring, secure compartment design, and security automation. These new security services are part of OCI's core design concepts, which include:
High Customer Isolation
Protection from firmware-based attacks
Ubiquitous data encryption
Automatic patches to the operating system
Sophisticated data protection
Oracle's emphasis on automation and user-friendliness aims to raise the bar for security by empowering all cloud users (not just those who are specifically tasked with security) to operate, develop, and scale in the public cloud securely.
Oracle Security Zones serve as distinct areas within OCI that enforce both implicit and explicit security regulations.
Additionally, OCI provides a maximum security zone that imposes a superset of mandated and prescriptive rules. These regulations can enforce a constant maximum security posture and help stop data exfiltration.
Policies that are enforced in Oracle Maximum Security Zones are:
-
No instances without hardened images
-
Only bastion access to hosts
-
All data encrypted with customer-managed HSM keys
-
No public internet in or out
-
No databases without backups
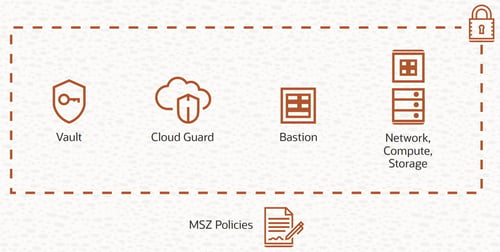
Because of the policies, resources within an Oracle Maximum Security Zone can only be moved to another Oracle Maximum Security Zone. Furthermore, to prevent configuration drift, the security configurations of an Oracle Maximum Security Zone cannot be disabled.
Oracle Cloud Guard is a unified security solution that offers a global and centralised approach to protecting customer assets and serves as the command centre for Oracle cloud security posture management.
As an aggregator, Oracle Cloud Guard gathers a variety of data from various native and non-native sources, including log, event, and threat intelligence data, across Oracle Cloud Infrastructure. In order to gain additional insights, such as information about a particular user or network address, the source data is frequently polled and fed into a detection and correlation engine.
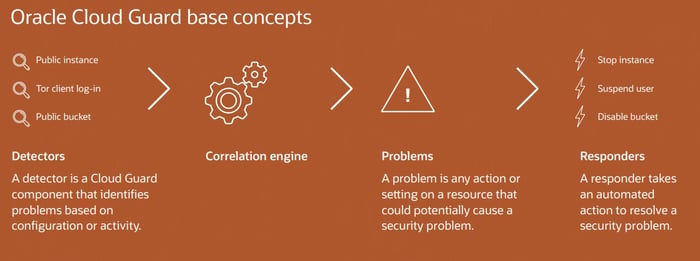
When Oracle Cloud Guard detects misconfigured resources or insecure activity drifts with a detector, it generates security problems that must be addressed. Detector recipes can be configured with additional conditional logic and are intended to be deployed as-is or customised to meet specific detection scenarios. Security issues are placed in a queue that can be filtered by risk level, compartment, problem type, and other criteria.
Administrators can use the responder's recipes to automate remediation of specific problem types, or they can refer to recommendations to remediate specific problem types. Oracle Cloud Guard provides a high-level overview of your security posture in Oracle Cloud Infrastructure with this capability. It provides the toolkit required to automate the remediation of minor security issues, as well as the granularity to delve deeper into more complex issues, allowing you to scale your security operations team.
According to the 2020 Oracle and KPMG Cloud Threat Report...
% of IT professionals are familiar with what’s called the cloud security shared responsibility model
But while most are familiar, few are experts. In the same report, it was revealed that...
Only % of IT professionals fully understand the cloud security shared responsibility model for all types of cloud services
Oracle Security Zones is helping to change this. Oracle is shifting the cloud security shared responsibility model so that the cloud service provider can provide additional assistance to the customer. Oracle Security Zones cover some of the layers of the shared responsibility model that IaaS customers were previously responsible for. Oracle Security Zones also improve configuration management, monitoring, and enforcement.
Furthermore, various enforcement points such as the control plane, the data plane, and Oracle Cloud Guard for reactive enforcement provide additional protection. As a result, customers will be able to focus more on the security strategy for the rest of their data and applications.
Oracle Security Zones can assist with the cloud security shared responsibility model in multiple ways, including:
Restricting public access to Oracle Cloud Infrastructure resources like databases and object storage buckets.
Enforcing the requirement that detached storage resources be housed in the same secure compartment as the compute instance.
Encrypting storage-related resources, such as block volumes, object storage buckets, and databases, using a customer-managed key.
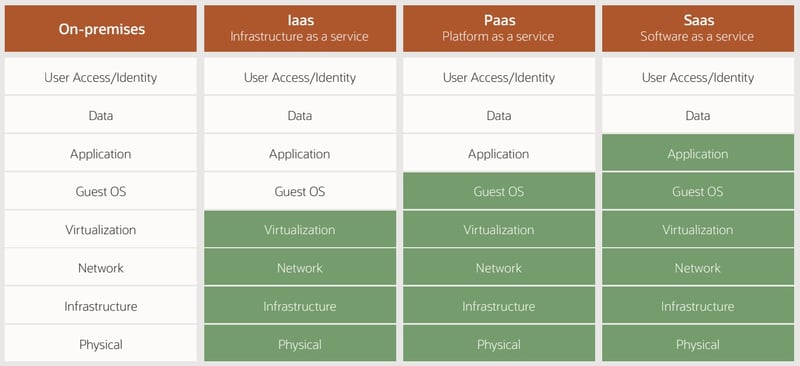
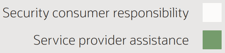
Without Oracle Security Zones
The cloud security shared responsibility model looks similar to the following example:
With Oracle Security Zones
Oracle will assist customers with the data, application, and guest OS layers.
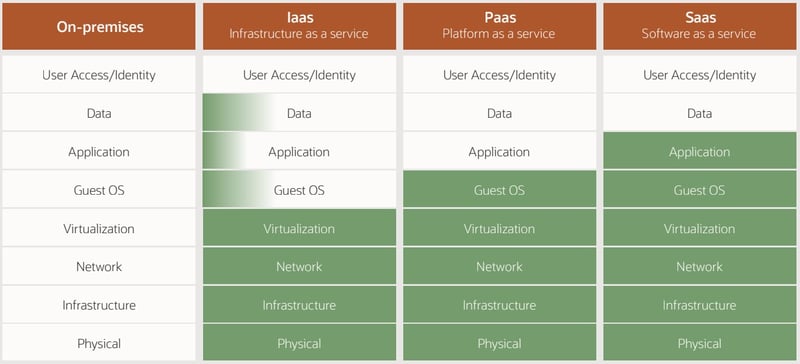
Control-plane enforcement policies in Oracle Security Zones include the following:
- At the data layer: The creation of block volumes and object storage buckets is prevented in the absence of customer-managed encryption keys (such as keys in Oracle Cloud Infrastructure Vault).
- At the application layer: Creating an internet gateway in VCN for public access is prevented.
- At the guest OS layer: The creation of a compute instance without a sanctioned image is prevented.
Oracle Cloud Infrastructure includes Oracle Security Zones and Oracle Cloud Guard, which are available to all cloud customers. With Oracle's approach, you can gain complete visibility of your global security posture and identify potential areas of risk.
You can reduce the barriers to deploying and maintaining security in the public cloud by using Oracle's approach to cloud security posture management. This includes the following:
Embedded security best practices
Oracle Security Zones provides implicit and explicit policies to help prevent the introduction of unauthorised cloud settings that jeopardises critical data.
Security for all Oracle Cloud users
Oracle Security Zones and Oracle Cloud Guard are available to customer tenancies on Oracle Cloud Infrastructure, delivered as infrastructure native services without the requirement for additional purchases.
Automated remediation
The built-in responders in Oracle Cloud Guard can generate alerts, launch multipath workstreams, or eliminate threats that pose a risk.
Centralised configuration management and monitoring
Oracle Cloud Guard monitors the entire Oracle Cloud Infrastructure ecosystem. It is a highly scalable and modular data-processing cloud security service that receives signals from Oracle and third-party sensors, detects areas of risk, and shuts them down before they can be exploited. To achieve the desired workflow of risk identification, validation, notification, and remediation, cloud security administrators do not need to stitch together multiple tools.
Find out more about Oracle Security Zones and Oracle Cloud Guard today with our Oracle Cloud Services and take your first step towards a new security posture.

You might also be interested in...
Cloud Revolutionises the Way Logistics Companies Operate
This resource discusses how cloud revolutionised the way logistics companies operate and how an optimised and modernised infrastructure can positively impact each part of a business.
Oracle Cloud: Reconstructing your approach to the cloud
Having a strong cloud strategy can provide the foundation for every function within an organization to be ready for whatever may come in the future.

Want to explore how Oracle can benefit your organisation?
Get in touch with our specialists today and start your Oracle journey with industry experts.


.png?width=250&height=56&name=stonewater-logo%20(1).png)



%20Oracle%20Database%20to%20Oracle%20Cloud%20Expertise/o-service-prtnr-OracleDBToOracleCloud-EMEA-UKIE-clr-rgb.png)

